Identity and Trust
Last Updated:
Analyst Coverage: Fran Howarth
Identity and access management (IAM) can be defined as the management of an individual’s identity, their authentication, authorisation for accessing resources and their privileges. It helps to implement good governance. The goal of IAM is to ensure that all resources are accessed in a secure manner and that users can gain access to the resources that they need, when they need them, to keep them productive.
In its original form, IAM generally applied to providing access to on-premise resources, with control firmly in the hands of the organisation. But things have changed as developments in technology have led to organisational perimeters being eroded. Cloud-based services have come into general use, mobile devices are now almost ubiquitous and organisations are increasingly looking to ensure the security and privacy of their customers’ digital identities. As a result, there has been a resurgence of interest in identity management.
Adversaries have become more sophisticated, increasingly targeting their attacks at specific organisations and individuals within them, often by misusing their access and entitlement credentials and looking to elevate to a higher level of privileged access having gained an initial foothold on the enterprise. According to Verizon’s Data Breach Investigations Report, stolen credentials are becoming an increasing problem, with 29% of all confirmed breaches and 60% of attacks against web applications involving the use of stolen credentials.
Organisations need to tackle these problems in order to engender trust that personal identity information is kept safe from both malicious attacks and inadvertent loss. This will help to shield them from reputational damage and from fines for failure to comply with regulations demanding strong security and privacy controls be applied to personal and sensitive data.
Some of the key trends being seen are discussed under the Emerging trends tab.
Identity management technologies and services extend trust across an organisation’s entire ecosystem, from on-premise applications and data stores to users and devices accessing resources remotely, often in the cloud and via mobile endpoints. Most vendors are extending their offerings to work across hybrid environments that incorporate both in-house and remote entities. ISO 24760-1: 2019, which defines a framework for identity management with an emphasis on IT security and privacy, states that an entity can have a logical or physical embodiment. It can be a person, device, group of such items, application, service or website, for example. This is important as networks expand to cover an increasing number of devices, including those that make up industrial networks and the Internet of Things, all of which need to have access controlled and authentication properly secured. Securely managing the identities and access rights of all across the network is important for establishing trust across the entire ecosystem.
Risk management is becoming increasingly important to organisations, especially given the rise in the volume and sophistication of cyber attacks that organisations face. Owing the high potential for damage from such attacks, security is increasingly coming to be seen as a severe risk that must be handled alongside all other risks that an organisation faces. Alongside risks from external attackers, organisations must handle risks that include fraud, insider threats, account takeover and business email compromise—all of which can be handled more effectively through identity management technologies and services.
Compliance issues are also on the rise. Although some industries are more highly regulated than others, regulatory compliance and adherence to industry standards impacts virtually every organisation. Many of these dictates demand that sensitive information is adequately secured against loss or theft and data protection requirements are becoming more stringent. GDPR is now a fact and not only drastically increases potential penalties for non-compliance, but has vastly expanded the definition of personal data and has given individuals much greater rights over how their personal data is handled. GDPR impacts any organisations that has dealings with EU residents, but similar legislation is now being passed in many jurisdictions worldwide to protect citizens beyond the reach of the borders of the EU.
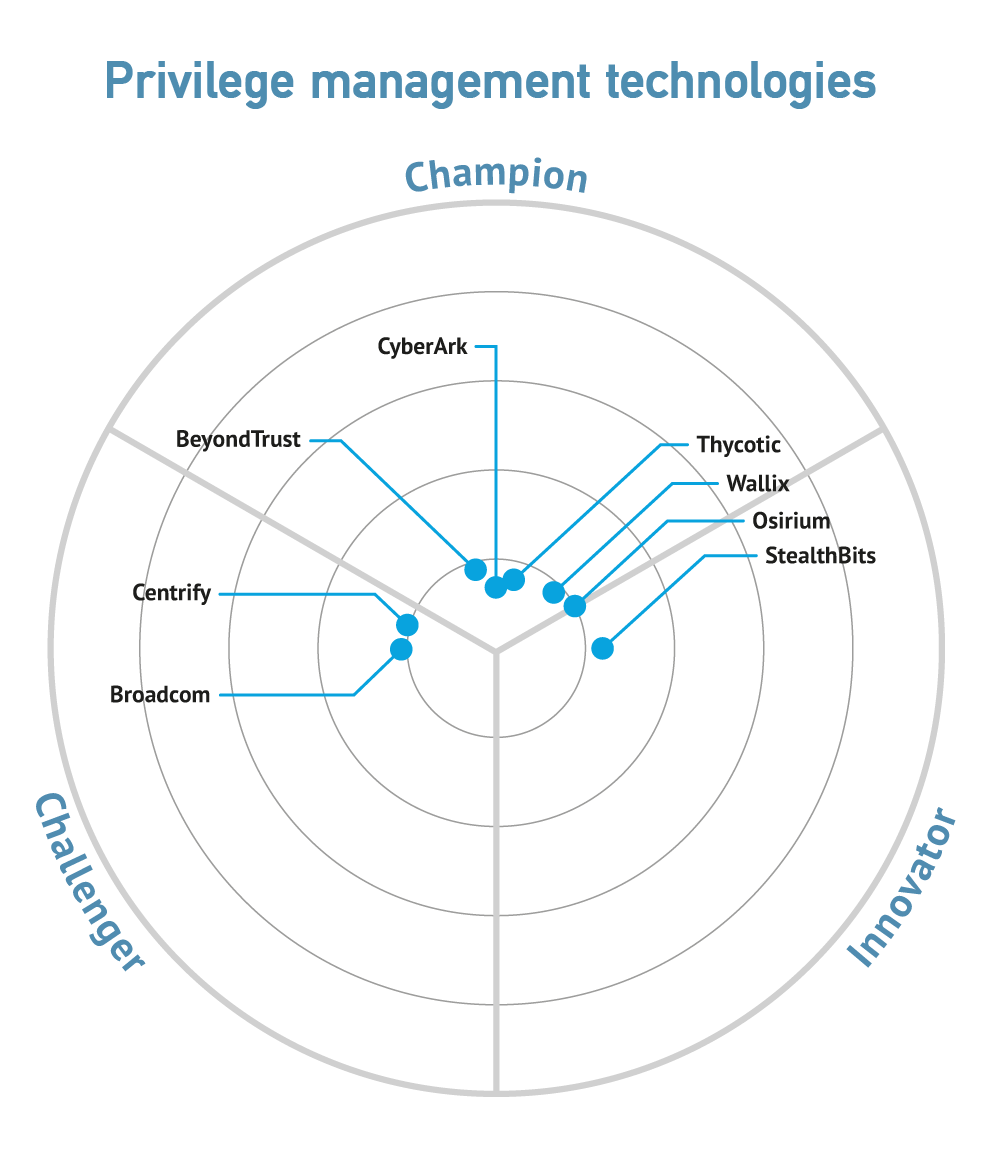
One of the biggest trends currently being seen in identity and trust is the emergence of privileged access management as a key priority for organisations, trickling down from large enterprises to organisations of all sizes in any industry. Privileged access management not only enforces the principle of least privilege, under which users are only given privileges that they need, sometimes just for one specific task before the entitlement is removed, but also reduces the risk of adversaries being able to escalate their access rights by gaining access to privileged accounts. Secure, multifactor authentication goes hand in hand with the need to secure sensitive data and enforce privileged access where it is needed. Privileged identity management is also becoming more important with the increased take up of DevOps, including provision of privileged task automation and for securing containers.
Context-based authentication and behavioural biometrics are also coming to the fore in order to provide more accurate assurance that a person really is who they say they are based on their behaviour and that of others in similar roles observed over time. Machine learning is often at the heart of these capabilities, helping organisations to create baselines of normal behaviour and analysing activity against what is expected to spot anomalous activity.
One other emerging trend that is interesting is the application of blockchain to identity and trust. Blockchain ledgers can be used to provide a historical record of activities related to access and authentication events stored in the blockchain which establishes a pattern of trusted behaviour. Related to the use of blockchain is the emerging concept of self-sovereign identities, which are under the complete control of the entity using them and not tied to any particular organisation, including governments that have traditionally been the source of verified and trusted identity. Since the entity retains complete control of the identity attestation, higher levels of security are introduced since no one can impersonate that person and delete identity information without the owner’s permission. These capabilities will become increasingly important in enabling person-to-person transactions.
Traditional vendors have been expanding their capabilities in the identity and trust space, moving from on-premise deployments to embrace needs that include growing use of cloud services and mobile devices, eventually moving out to industrial environments and devices that make up the Internet of Things. Many have also developed offerings for catering for the digital identities of customers, as well as partners and suppliers.
Some of these vendors have a fairly wide offering in the IAM space as part of a wider security portfolio, as well as products in other technology areas. These include some of the largest and best-known technology vendors.
There are also a number of specialised identity and trust vendors, with many focused on a particular field within identity and trust, such as privileged access management.
Commentary
Solutions
These organisations are also known to offer solutions:
- Adaptive Shield
- Atos
- AWS
- Centrify
- Core Security
- CSI Tools
- Fischer International
- ForgeRock
- HID Global
- Hitachi ID
- Micro Focus
- Okta
- One Identity
- OneLogin
- Open IAM
- Oracle
- Osirium
- Ping Identity
- RSA
- SailPoint Technologies
- Simeio Solutions
- STEALTHbits
- Symplified
- Thycotic
- Wallix