Threat Detection and Response
Analyst Coverage:
Threat detection and response is concerned with ensuring that organisations have access to sophisticated technology to defend themselves against the complex threat landscape that they face. Security investments have traditionally favoured a preventive approach, trying to stop threats from entering the network in the first place.
However, over the past 15 to 20 years, there has arisen a great focus on detecting threats that have made it through preventive controls to gain a foothold on the network. The aim is to uncover both known and unknown, hidden or emerging threats as quickly and efficiently as possible in order to limit the damage that they can cause. But, it goes further than that by helping organisations to respond to threats that are uncovered in an efficient manner.
There are many flavours of threat detection and response, from pure technology to technology plus services. Originally, SIEM (security information and event management) systems were developed for the threat detection piece, but they were limited in their capabilities, especially in terms of response. Despite this, they are now considered to be foundational technologies for many organisations and many of the new technologies that have been developed still integrate with them.
In terms of technology, many new offerings have been developed in response to the need for wider coverage across the network. Endpoints continue to proliferate, something that became apparent from 2010 onwards as smartphones came out and have been widely taken up. This led to the development of EDR (endpoint detection and response) technology that continuously monitors endpoints for suspicious activity so that action can be taken. Shortly after, UEBA (used and entity behavioural analytics) was added to the mix, which focuses directly on user and device behaviour to add further context to investigations. For better response capabilities, SOAR (security orchestration, automation and response) technology was developed to aid organisations in achieving their desired security outcomes, guiding organisations through the steps required in responding to incidents.
More recently, these technologies have been combined into XDR (extended detection and response) technology to provide a more holistic detection and response capability. NDR (network detection and response) has also been brought into the mix, extending capabilities for detection across all parts of the network.
But threat detection and response requires more than technology alone and this is where MDR (managed detection and response) capabilities come into play. These combine the provision of technology with access to expertise from the service provider to help organisations that are battling to make the best of these complex new technologies, especially when skilled security personnel are hard to find and retain or where organisations lack sufficient budget to adequately staff their security function. Many service providers have now embraced XDR in their offerings and this sector has shown and will continue to show rapid growth.
Threat detection and response works by taking telemetry feeds from systems throughout the network, both in terms of controls installed on premises and in their extended networks. These feeds provide detailed information related to all activity seen by correlating and analysing the data to uncover trends and patterns. Detailed metadata reports are produced that are far superior to alerts that had been overwhelming organisations as this information had to be sifted through to find out if a threat was real and to identify its severity.
Machine learning is an essential part of these technologies, which uses advanced algorithms to detect anomalies that help to uncover new and emerging threats and provide greater context to improve the speed, efficiency and accuracy of decision making.
Another key component is threat hunting, which can be automated or driven by human expertise and which relies heavily on threat intelligence, that looks to proactively root out unknown, hidden and emerging threats that could otherwise be missed.
Every organisation, no matter its size or industrial focus, is liable to be seen as a viable target by adversaries. Large organisations that have extensive security teams may choose to install the technologies themselves, especially where they have a fully staffed security operations centre. However, even then they may wish to engage with an MDR provider to gain access to expertise that will function as an extension to their security team.
Some other organisations that have limited security teams to understand and deal with the complexity of the technology are prime candidates for MDR services, which are often offered in tiered support levels, with some offering just out-of-hours support.
Every organisation also faces regulatory compliance challenges. Whether the organisation is in a highly regulated sector or just subject to data protection requirements, threat detection and response technologies can help them to ensure that they are keeping up with and meeting compliance objectives by rooting out security gaps that can hinder their compliance programmes.
Threat detection and response is a vibrant space that will continue to grow in importance as new threat challenges need to be faced.
Networks are expanding rapidly to incorporate supply chains, industrial systems and the cloud. In particular, use of cloud has been increasing rapidly and has been given a boost by digital transformation efforts and by remote working, which has been a key development during the pandemic. Most threat detection and response technologies are based in the cloud, with many being offered on a subscription basis. By placing technologies in the cloud, capabilities can scale to a much greater extent than traditional technologies.
Particularly in the MDR sector of this market, services are being extended to cater for the needs of the midmarket, packaged for easy uptake and consumption. Rather than having to purchase and implement technologies, these are provided by the MDR service, along with access to expertise. They can also gain access to technologies such as SOAR that were largely the preserve of larger organisations that had the time and expertise to exploit them to their full potential.
Response is also gaining traction. Vendors in this space have spent time building out detection capabilities, but response capabilities largely lagged behind. This is changing rapidly, with vendors embedding SOAR into their offerings and with MDR providers offering expert guidance in this area. This is expected to be a key focus for this year and going forward.
Another emerging area is a greater focus on identity management, particularly with regard to privileged accounts and entitlements that are a prime target for attackers. This is also something that is likely to expand over the coming year and beyond.
SIEM is seeing a resurgence in interest as a data ingestion point for data flows from other threat detection and response technologies. Four of the core vendors are public companies. Exabeam, a relative newcomer to the space, received substantial funding in 2021 to reach a valuation of $2.4 billion. Both LogRhythm and RSA Security, which has its NetWitness product, were acquired by private equity. Both have substantial product portfolios surrounding their SIEM offerings.
EDR vendors have been rebranding over the past couple of years, with most moving from a focus solely on EDR to develop into XDR platforms. Previously, many had touted themselves as MDR vendors in order to offer managed services, primarily for their own products. Whilst still offering managed services in some cases, many have now moved to focus primarily on their XDR technology platforms. In recent years, some vendors have been acquired, namely Carbon Black by VMWare towards the end of 2019, Cylance by BlackBerry and Symantec by Broadcom. No such acquisitions have been seen in the past year or so, but FireEye and McAfee enterprise security division were acquired by private equity and merged to form Trellix. There have not been many in this market sector that have received substantial funding recently.
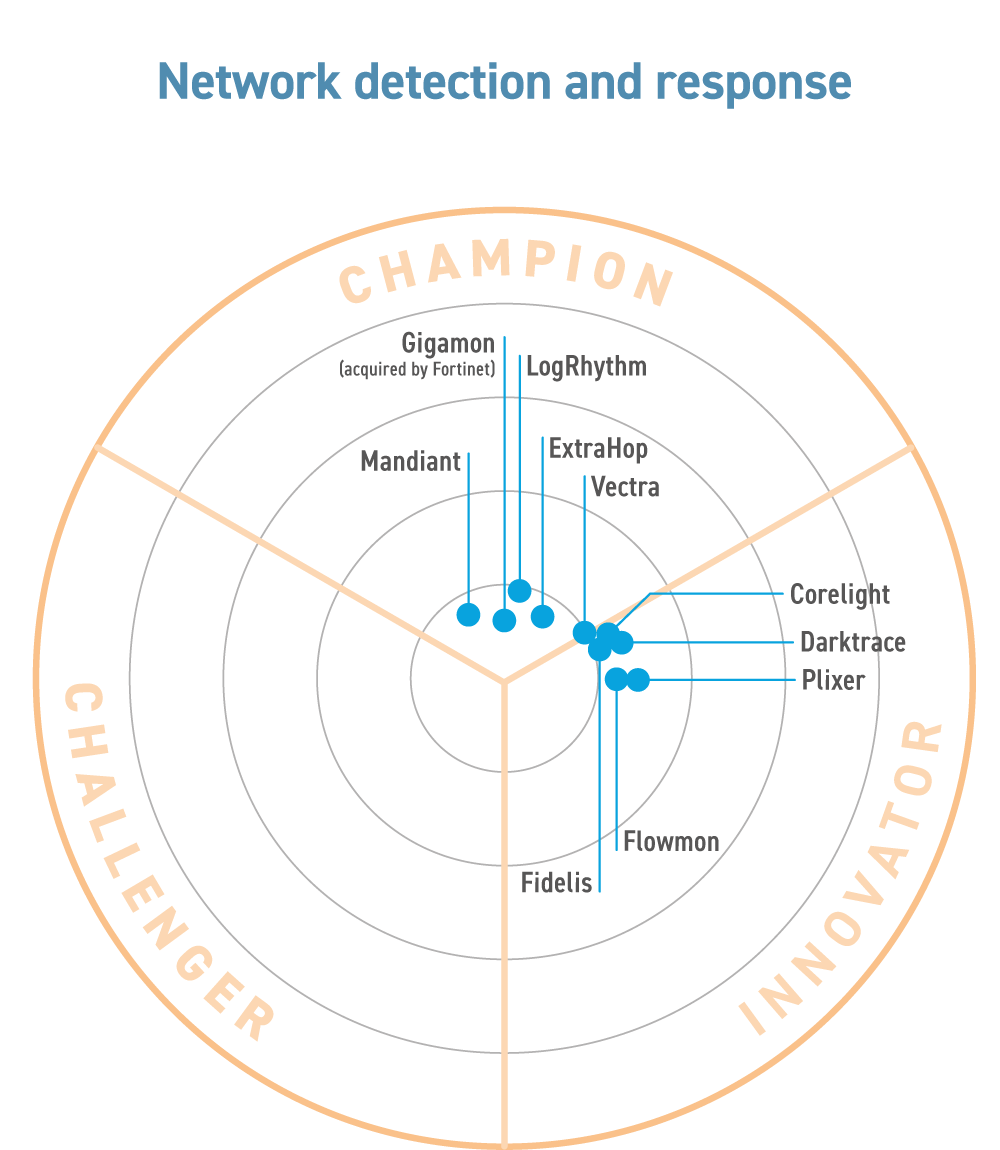
In rounding out their offerings, many XDR vendors, as well as MDR service providers, have been partnering with NDR vendors to add telemetry from the network and to expand beyond a core focus on endpoints. This market segment is characterised by some smaller vendors, as well as those that have recently seen valuations exceeding $1 billion, including Vectra AI. ExtraHop was acquired by private equity in 2021 and Flowmon by Kemp Technologies, which itself was acquired by Progress Software in 2021. Both Corelight and Vectra AI received substantial additional funding in 2021.
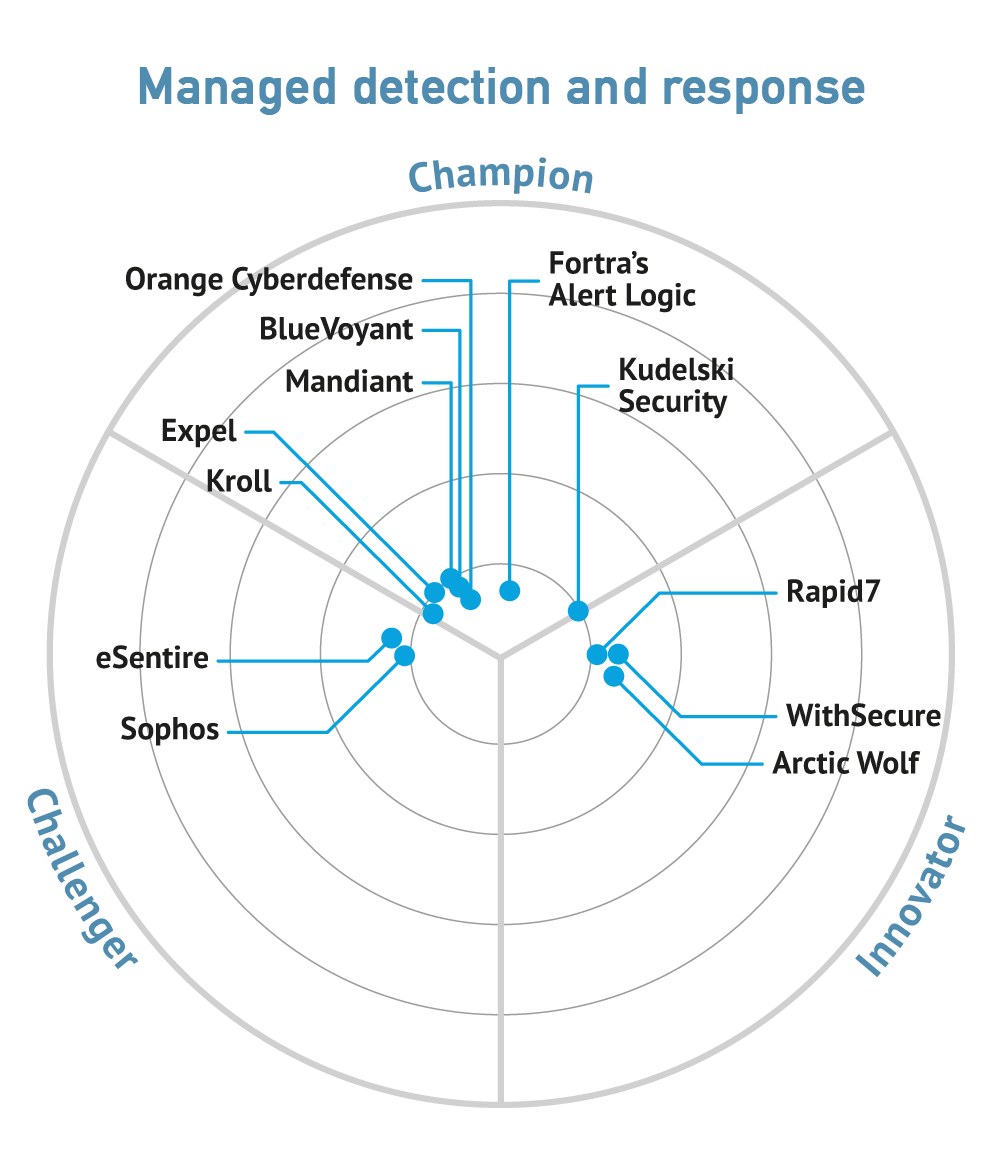
The MDR market, which contained a confusing array of vendors, has come into its own. Technology-agnostic vendors now dominate this market, taking feeds from a wide range of sources that include endpoints and the network. This is a dynamic market sector. Alert Logic was acquired by HelpSystems in April 2022, Redscan by Kroll in March 2021, Mandiant by Google for $4.5 billion in September 2022 and Sophos by Thoma Bravo in February 2020. In July 2022, F-Secure split out its enterprise business to form WithSecure in 2022. There are two public companies among the top MDR vendors—Orange Cybersecurity and Rapid7. Some have received substantial funding over the past couple of years, including Arctic Wolf, BlueVoyant and Expel. All the major vendors are seeing high levels of growth in the MDR space, with several valued at more than $1 billion. The majority are expanding their offerings in the areas of cloud, incident response, identity that includes zero trust, more integrations for expanded telemetry, and a greater focus on risk management and resilience.
Related Blog
- Key ways managed detection & response (MDR) helps with compliance
- The long tail – the hidden face of IT
- ExtraHop forging ahead in the NDR market
- How vendor partnerships will benefit your business
- Orange Cyberdefense MDR
- Is a managed WAF service a good fit for your organisation?
- Scality’s ARTESCA virtual appliance
- Ransomware just met its match
- If it’s not integrated, don’t fall for it
Related Research
- Managed Extended Detection and Response, by Rapid7
- Viavi Observer Platform
- Continuous threat exposure management
- ExtraHop Reveal(x)
- Fortra Alert Logic (2023)
- Network Detection and Response (2023)
- Expel – Security Operations Provider
- How cybersecurity investments will benefit your business
- Kudelski Security’s MDR services
- Managed Detection and Response Services (2023)
Related Companies
Connect with Us
Ready to Get Started
Learn how Bloor Research can support your organization’s journey toward a smarter, more secure future."
Connect with us Join Our Community