The importance of endpoints to security
Published:
Content Copyright © 2020 Bloor. All Rights Reserved.
Also posted on: Bloor blogs
This is the second part of Bloor analyst Fran Howarth’s series of blogs on MDR looks at endpoint security. Click here to read the first part, or click here to read part 3.
At the core of managed detection and response (MDR) services is endpoint security. Taken at its broadest definition, an endpoint in computing terms is the entry point to a service.
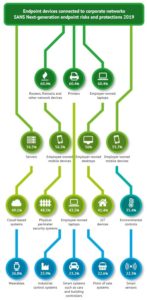
Long gone are the days when an endpoint can be defined as just a piece of hardware used by an individual, such as a PC, workstation or mobile device. These days, endpoints are not just purely end user devices but rather can be anything connected to a network, including industrial systems and medical devices. Estimates vary widely, but the number of IoT connected devices are said to number in the billions. The types of endpoints that connect to corporate endpoints are shown in the figure below.
Convenience vs security
End user endpoints provide a convenient way to access resources and the more mobile they are, the more convenient they are. Cloud services are now widely in use and are used for storing an ever increasing amount of information, including that which is sensitive or confidential. Endpoint devices are used to access such services and to transmit and use much of that information. Even when the information is not stored elsewhere, endpoints such as smartphones can themselves contain vast swathes of information. And the apps that are installed on them are not always trustworthy as they are capable of leaking information and often require that users grant access to more information than the app needs. They can also be lost or stolen and access credentials for devices, applications and cloud services are too easily compromised.
IoT devices are rarely adequately secured either. Yet, devices such as medical equipment that are connected to networks contain extremely sensitive information and security researchers have demonstrated how hacking them could be life threatening.
As endpoints have proliferated, adversaries have increasingly used them as a conduit for infiltrating networks and services with malicious threats. According to the Ponemon Institute, 68% of respondents reported in 2019 that they had experienced one or more endpoint attacks that successfully compromised data assets and/or IT infrastructure during the year, up from 54% in 2017. The cost per endpoint breach is also skyrocketing, averaging $9 million in 2019, up more than $2 million over 2018.
Hence, this is why endpoints are so important and why their defence is central to MDR services and protecting them, detecting threats and responding to incidents impacting endpoints is core to MDR.