User and Entity Behavior Analytics
Last Updated:
Analyst Coverage: Fran Howarth
User and entity behaviour analytics (UEBA) technologies focus on identifying patterns of user and device activity that are outside of the normal patterns of expected behaviour in order to identify activity that could be suspicious or clearly malicious.
Why is it important (hot)?
UEBA technologies build on the capabilities of other technologies used for monitoring activity on networks, including security information and event management (SIEM) systems and data loss prevention tools. They are particularly useful for the detection of insider threats, advanced attacks that have gained a foothold on the network and malicious activity such as financial fraud by providing contextual information regarding what users are doing with network resources, applications and data.
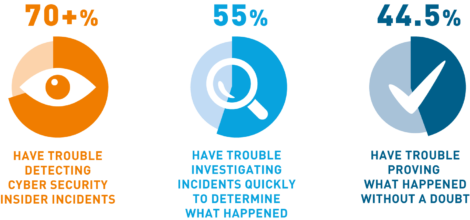
Because UEBA technologies provide detailed contextual information tying actions taken to specific devices and users, they provide security operations personnel with faster investigations and root cause analysis. This enable personnel to accurately focus their efforts, so adverse situations can be solved quickly and efficiently.
How does it work?
UEBA technologies employ a specialised form of security analytics that focuses directly on user behaviour. They work by extracting information related to events across the network from security controls such as SIEM systems, security logs, identity and access management tools, data loss prevention systems and other data sources including HR databases and industry-specific applications. The data collected is then analysed to establish baselines of behaviour considered to be normal so that any activity seen that is outside of normal can be flagged. Machine learning models are deployed to build the baselines of behaviour by looking at historical data to establish what is normal for each user and device, comparing this behaviour with that of comparable roles. The data collected is then aggregated using risk scoring methodologies to create a score for each user related to perceived risk. When anomalous behaviour is seen, relevant information that includes context such as a person’s roles, responsibilities and level of risk is sent to analysts so that they are able to investigate a particular user’s behaviour.
UEBA technologies use advanced algorithms and machine learning to detect anomalies that signify potential threats such as the presence of malware or a user engaged in suspicious activity. The information that is uncovered is combined with privacy controls for automated compliance with global privacy regulations, including those regarding the monitoring of user and entity behaviour. For example, they can help to achieve some of the more onerous requirements of the general data protection regulation in an automated fashion.
UEBA technologies enable organisations to improve efficiency and manage risks more effectively whilst avoiding financial loss and reputational damage. They add value by giving organisations the ability to prevent attacks, especially those originating from inside the network, detecting breaches faster to reduce exposure and mitigating the damage caused by cyber threats. Using such technologies would help organisations to faster and more easily detect and respond to threats. The impact of some of the largest hacks of all time, including those against the US State Department Sony, Target and Home Depot, which ended up costing a total of $179 million, could have been greatly lessened.
Organisations that deploy good security and risk management practices and processes will engender trust among customer and business partners. Thus, they can actually act as a business enabler and greatly help organisations to meet their obligations with regard to data privacy and security, as well as compliance objectives.
Quotes
“In addition to identifying and stopping insider threats, the bank also discovered additional layers of financial fraud being conducted by those insider threats.”
Fortune 50 global bank
“People have very definite patterns of behaviour and looking at behavioural analytics is about how we take those patterns and start to get useful information out of them.”
Gabe Barrett, information security consultant
“CEOs and other risk professionals will be able to make more informed decisions about how to run their organisations and allocate resources. Risk measurements allow leaders to compare effectiveness based on quantifiable impact.”
Adapted from Bay Dynamics
UEBA technologies provide incremental value to a number of complementary technologies widely used in enterprises, including SIEM systems and DLP, by providing deeper analytic capabilities regarding what users, devices, assets and applications are doing on the network and the impact of those actions.
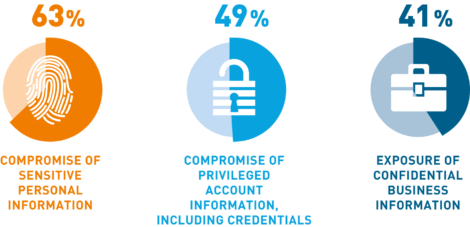
As with many technologies, many organisations will wish to pick one or two specific use cases related to problems encountered within their networks in order to prove the value of the technology before undertaking a wider implementation. Among the main use cases to consider are finding compromised credentials, accounts and devices to prevent unauthorised access to sensitive data, uncovering malicious, whether intentional or not, activity being undertaken by legitimate trusted insiders, preventing data from leaving the network when the action is not authorised, and uncovering and managing fraud. UEBA technologies will help considerably in protecting personal data from compromise, thus helping organisations with their data protection responsibilities, such as adherence to GDPR.
The Bottom Line
Once seen merely as insurance, security technologies such as UEBA enable a business by reducing potential financial losses and enhancing productivity. By understanding what users are doing and how they interact with applications and data, organisations can better prioritise their investments to improve their security posture overall and enabling them to more easily meet privacy and compliance objectives.
Commentary
Coming soon.
Solutions
Coming soon.
Research
Coming soon.