Security? what security?
We live in a world now that whatever you read you are bound to come across the word “Security” in some form. This word covers a whole gamut of meanings, so let’s go back to basics of a simple definition: “Security is about freedom from doubt, anxiety, fear; risk or danger; safety. It also has associated with this meaning the context of confidence in that freedom.”
Now if we then added the little word of IT in front, we have one of the bains of the IT manager as Nigel Stanley, Bloor Research’s Practice Leader for Security explains, “IT security comprehensively covers the whole remit of protecting and defending business or organisational systems and data from unwelcome attacks or intrusions. This large area includes protection from the outer edges of the security domain such as handheld devices through to network perimeter, inside threats and local defenses. It looks at the ever growing threats, many of them new and innovative. It includes use of firewalls, data loss prevention, data encryption, anti-malware, database protection, identity management, intrusion detection/prevention, content management/filtering and security policies and standards.”
But why should you be concerned? Business Link, in their guide to IT Security state, “The security of business IT systems has never been so important. Businesses rely more and more on IT to support their activities, and this makes them increasingly vulnerable to threats from hackers, viruses and even their own staff. Having the correct information at the right time can make the difference between success and failure for your business. Effective security can help you control and secure information from malicious changes and deletions or from unauthorised disclosure.” The manufacturing sector has harnessed the power of IT to underpin improvements in productivity, process efficiency and higher quality supply chains. Like every other industry, the sector also has to cope with a sharp increase in flexible working arrangements and growing security challenges. Ravi Pandey, Senior Vice President and UK Head, NIIT Technologies, explained, “IT managers are alarmed about the increasing use of social networks and social media by employees while at work. Research has shown that employees using applications on social networks while at work is the largest single security concern for IT managers and when staff members download unapproved applications, this can lead to the infections of systems via viruses. With many organisations outsourcing their IT, it is essential all due diligence is carried out.”
Dave Mount, Technical Director, UK & Ireland of NetIQ, told me, “Enforcing security policy is a challenge for enterprises. IT process automation can step in and ensure that there is a consistently applied and controlled procedure for managing access to critical data and applications. It is this capability to sustain the highest levels of security without deviation that underpins the role of ITPA in network security. This not only delivers a secure environment but also ensures an organisation complies with prevalent information governance requirements.” Real prevention starts from having in place robust identify management systems that are consistently applied and controlled,
Components of IT Security
As usual, IT security terminology is often incorrectly interchanged. The terms information security, computer security and information assurance are not the same. These terms are interrelated and share the common goals of protecting the confidentiality, integrity and availability of information; however, there are some subtle differences between them. These differences lie primarily in the approach to the subject, the methodologies used, and the areas of concentration. Information security is concerned with the confidentiality, integrity and availability of data regardless of the form the data may take: electronic, print, or other forms. Computer security can focus on ensuring the availability and correct operation of a computer system without concern for the information stored or processed by the computer.
Information Security
For some 20 years, information security was seen as based around three pillars (known as the CIA triad) which are:
- Confidentiality: protecting information from unauthorised disclosure;
- Integrity: protecting information from unauthorised modifications, and ensure that information is accurate and complete; and
- Availability: ensuring information is available when needed.
Donn Parker proposed an alternative model that he called the six atomic elements of information (also known as the Parkerian Hexad). The elements are confidentiality, possession, integrity, authenticity, availability, and utility. The new concepts can be viewed as follows:
- Possession or Control: is concerned with a loss of control or possession of information but does not involve the breach of confidentiality;
- Authenticity: refers to the truth of the claim of origin or authorship of the information; and
- Utility: means usefulness
Computer Security
Computer system security is concerned with the collective processes and mechanisms by which sensitive and valuable information and services are protected from publication, tampering or collapse by unauthorized activities or untrustworthy individuals and unplanned events respectively. The strategies and methodologies of computer security often differ from most other computer technologies because of its somewhat elusive objective of preventing unwanted computer behavior instead of enabling wanted computer behavior. The technologies of computer security are based on logic.
Information Assurance
Information assurance (IA) is the practice of managing risks related to the use, processing, storage, and transmission of information or data and the systems and processes used for those purposes. While focused dominantly on information in digital form, the full range of IA encompasses not only digital but also analog or physical forms. There are three models used in the practice of IA to define assurance requirements and assist in covering all necessary aspects or attributes:
- Information security model, also called the CIA Triad, which addresses three attributes of information and information systems, confidentiality, integrity, and availability.
- The Five Pillars of IA model, promulgated by the U.S. Department of Defense, deals with the measures that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation.
- The Parkerian Hexad, first introduced by Donn B. Parker.
Understanding the Standards
The key standard in the UK is BS ISO/IEC 27001, whose main objective is to help establish and maintain an effective information management system. The standard covers all the main security issues from a manager’s viewpoint and goes into significant depth in explaining good practice. The standard is divided into ten main sections—each of which is key to maintaining security. These are:
- Security Policy – explains what an information security policy is, what it should cover and why your business should have one.
- Organisational Security – explains how information security should be managed in a business.
- Asset Classification and Control – assets include the information itself, computers, software and even services. These could all be valuable and need to be managed and accounted for.
- Personnel Security – personnel issues such as training, responsibilities, vetting procedures, and how staff respond to security incidents.
- Physical and Environmental Security – physical aspects of security including protection of equipment and information from physical harm, keeping key locations secure as well as physical control of access to information and equipment.
- Communications and Operations Management – appropriate management and secure operation of information processing facilities during day-to-day activities. This specifically includes computer networks.
- Access Control – control of access to information and systems on the basis of business and security needs. Access control is concerned with controlling who can do what with your information resources.
- System Development and Maintenance – some businesses develop their own software. This part of the standard deals with the issues that are associated with the design and maintenance of systems so that they are secure and maintain information integrity.
- Business Continuity Management – addresses the maintenance of essential business activities during adverse conditions, from coping with major disasters to minor local issues.
- Compliance – concerns business compliance with relevant national and international laws.
What should I be aware that is new for this year?
Corey Nachreiner, Senior Security Analyst at WatchGuard, has put forward the following predictions for 2010:
- Social Networks: The #1 Malware Source – Neilson Online says social networks have become more popular communication tools than email. Social networks, by their very nature, are gathering places, which tends to imply increased levels of trust. Lastly social networks leverage complex, Web 2.0 technologies that can suffer serious security vulnerabilities.
- Third‐Party Programs Get Pwned – OS vendors have fixed most of the obvious flaws so the code in their popular client applications for web browsing and email is more secure, and the patch cycle is well established and often automatic. Nachreiner sees that hackers will target 3rd part applications such as Adobe Flash, Sun Java, and Adobe Reader.
- Smart Phones Get Hammered –A smart phone is simply a mobile phone that has all kinds of extended PC-like services, such as web browsing, email, and sometimes even word processing. They increase your phone’s attack surface. Now add to this scenario the number of smart phones in use. Nachreiner predicts that every popular smart phone will suffer at least one attack during 2010.
- Data Loss Prevention Makes Big Gains – As technologies that directly protect data, things like local hard drive encryption and DLP (data loss prevention) solutions are adopted by SMBs..
- Windows 7 Suffers Critical Zero Day Vulnerability –Windows 7 reversed some of Vista’s security capabilities. Nachreiner expects at least one critical, zero day Windows 7 exploit to surface in the next 12 months.
- Cloud Computing: Half Haven, Half Storm – Nachreiner expects at least one major cloud service security breach, which will bring some of a number of the security issues I raised in the previous article on Cloud computing security issues to a head. On the other hand, cloud-based security solutions will thrive in 2010.
- Mac Threats Double – In 2009, Apple fixed hundreds of vulnerabilities in its OS and supporting products and Apple users began to see increased examples of Mac malware. Nachreiner believes that Mac users should expect to see twice as many Mac threats in 2010.
- Poisoning The Information Well – Nachreiner expects major SEO (search engine optimization) poisoning attacks to surface in 2010, and he suggests you remain wary of your web search results.
This sounds like a big headache. So what should I do to ensure my organisation is adequately and effectively protected?
Getting the ground rules in place
It is important to have an effective set of policies and procedures in place which are constantly kept up-to-date. They are crucial to implementing an effective information security strategy. They should be viewed as the glue that holds all aspects of information security together, without them each aspect of information security would be a collection of disparate parts. For policies to be effective, they must reflect the organizations’ specific requirements. But the key is to identify what you are vulnerable to and concentrate on that. Pandey explained that NIIT conducts a vulnerability assessment in order to highlight vulnerabilities that an attacker could exploit in an organisation’s system. There are a number of consultancy companies who provide similar services.
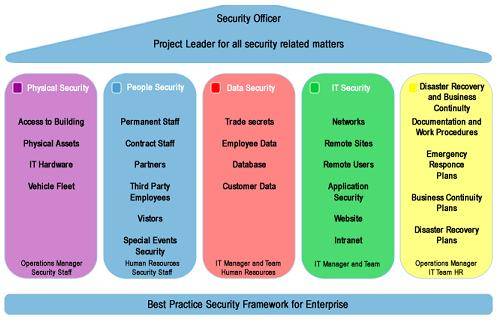
Figure 1 : Security Policy Framework (Source: VigiTrust Ltd)
So where can you go to, to find guidelines to help you get started? Business Link has issues a number of useful introductory texts that provide some good basic advice. The Information Security Forum (ISF) is an independent, not-for-profit organisation that supplies authoritative opinion and guidance on all aspects of information security. It has produced a Standard of Good Practice and as a basic guide I have found this a useful starting point. This presents a comprehensive set of practical and measurable information security-specific controls. The main aspects covered are:
- Security Management (enterprise-wide) – this relates to high-level direction for information security, arrangements for information security across the organisation, and establishing a secure environment.
- Critical Business Applications – this relates to requirements for securing business applications, identifying information risks and determining the level of protection required to keep information risks within acceptable limits.
- Computer Installations – this relates to the design and configuration of computer systems, management activities required to establish a secure computer installation and maintain service continuity.
- Networks – this relates to network design and implementation, management activities required to run and manage secure networks, including local and wide area networks, and voice communication networks.
- Systems Development – this relates to the application of information security during all stages of systems development, including design, build, testing and implementation.
- End User Environment – this relates to local security management, protecting corporate and desktop applications, and securing portable computing devices.
What ever size of organisation you are, your information is a critical resource that you have to protect. But not all information is equal in importance, so you do need to understand what information is critical to your business, and also what information you share with external sources, such as customers, suppliers and partners. You also need to set up some basic security levels, such as locked room for servers, user ids and passwords, security entry cards. Always remember that security needs to be actively managed in your organisation.
This article appeared in The Manufacturer earlier this year.
